MIKROTIK IPSEC TRE SEDI OVERLAPPING

MIKROTIK IKEv1 NETMAP GNS3
In questo articolo, simuliamo tre sedi Mikrotik interconnesse con IPSEC IKEv1, ipotizzando un fenomeno di overlapping tra due sedi – Laboratorio virtualizzato con GNS3.
Componenti utilizzati:
- Un CHR Mikrotik
- Due connessioni internet con IP PUBBLICO.
- Una connessione internet con IP NATTATO.
Livello difficoltà: Medio-alta
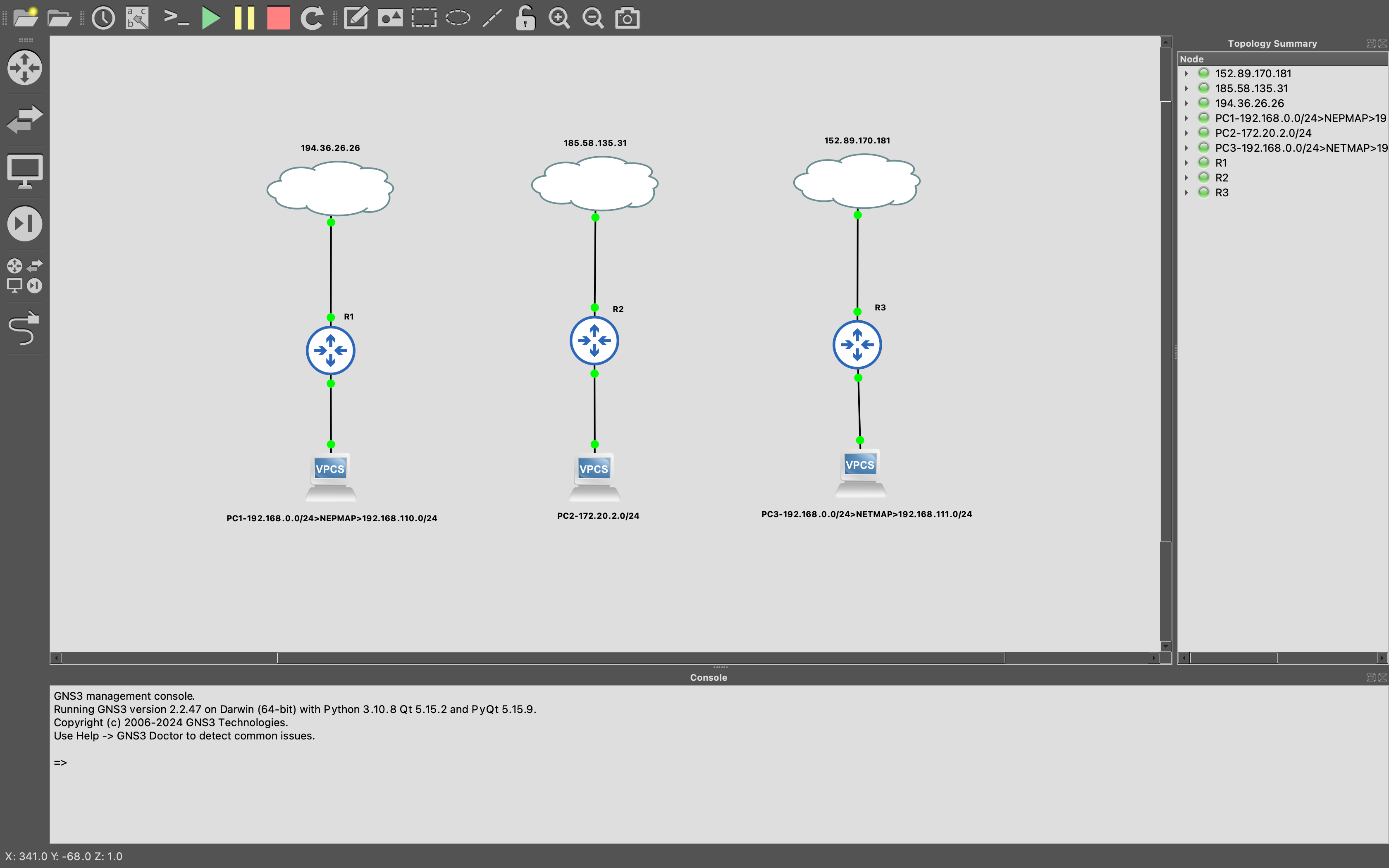
Come possiamo osservare dal diagramma, interconnettiamo tre reti con ip pubblici differenti tramite IPSEC IKEv1.
Con le IPSEC policy, facciamo comunicare direttamente le tre sedi.
Visto la presenza di una sovrapposizione delle LAN dei Router 1 e 3, inseriamo delle regole per rimappare le subnet delle due reti.
Potrai scaricare il progetto gns3 di questo articolo sia con i tre router già configurati.
In alternativa lo puoi scaricare con i 3 Router resettati e configurarli da zero utilizzando gli export dei tre router che troverai di seguito.
Le credenziali di accesso ai Router sono:
- user1
- 2024-LABIPSEC!
Si raccomanda di sostituire le password al primo accesso impostando delle password sicure in quanto le medesime vengono postate pubblicamente.
1. Configurazione Router 1
Qui di seguito un export completo della configurazione del Router 1 :
/interface vlan
add interface=ether1 name=vlan80 vlan-id=80
/interface pppoe-client
add add-default-route=yes disabled=no interface=vlan80 name=pppoe-out1 \
password=HNNIWJCQ user=Syntho194.36.26.26
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-256 hash-algorithm=sha256 name=\
profile-IKEv1-ph1
/ip ipsec peer
add address=185.58.135.31/32 name=peer-->R2 profile=profile-IKEv1-ph1
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=proposal-IKEv1-ph2 \
pfs-group=modp2048
/ip pool
add name=pool1 ranges=192.168.0.2
/ip dhcp-server
add address-pool=pool1 interface=ether2 name=server1
/port
set 0 name=serial0
/ip address
add address=192.168.110.1/24 interface=lo network=192.168.110.0
add address=192.168.0.1/24 interface=ether2 network=192.168.0.0
/ip dhcp-client
add add-default-route=no interface=ether1
/ip dhcp-server network
add address=192.168.0.0/24 dns-server=1.1.1.1 domain=WORKGROUP gateway=\
192.168.0.1 netmask=24
/ip firewall address-list
add address=192.168.111.0/24 list=remote-lan
add address=172.20.2.0/24 list=remote-lan
/ip firewall filter
add action=accept chain=input connection-state=established,related
add action=drop chain=input connection-state=invalid
/ip firewall nat
add action=netmap chain=dstnat comment=\
NETMAP192.168.0.0/24<---->192.168.110.0/24 dst-address=192.168.110.0/24 \
src-address-list=remote-lan to-addresses=192.168.0.0/24
add action=netmap chain=srcnat dst-address-list=remote-lan src-address=\
192.168.0.0/24 to-addresses=192.168.110.0/24
add action=accept chain=srcnat comment=allow_ipsec_to-R2 dst-address=\
172.20.2.0/24 src-address=192.168.110.0/24
add action=accept chain=srcnat comment=allow_ipsec_to-R3 dst-address=\
192.168.111.0/24 src-address=192.168.110.0/24
add action=masquerade chain=srcnat ipsec-policy=out,none out-interface=\
pppoe-out1 src-address=192.168.0.0/24
/ip ipsec identity
add peer=peer-->R2 secret=prova1@2
/ip ipsec policy
add comment=link-to-LAN-R2 dst-address=172.20.2.0/24 peer=peer-->R2 proposal=\
proposal-IKEv1-ph2 src-address=192.168.110.0/24 tunnel=yes
add comment=link-to-LAN-R3 dst-address=192.168.111.0/24 peer=peer-->R2 \
src-address=192.168.110.0/24 tunnel=yes
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system identity
set name=R1
/system note
set note=\
"Questo Router e' stato utilizzato con PPPOE su vlan 80 e IP pubblico"
2. Configurazione PC1:
ip dhcp
set pcname PC1
save
3. Configurazione Router 2
Qui di seguito un export completo della configurazione del Router 2:
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-256 hash-algorithm=sha256 name=profile-IKEv1-ph1
/ip ipsec peer
add address=194.36.26.26/32 name=peer-->R1 profile=profile-IKEv1-ph1
add address=152.89.170.181/32 name=peer-->R3 profile=profile-IKEv1-ph1
/ip ipsec proposal
add auth-algorithms=sha256,sha1 enc-algorithms=aes-256-cbc name=proposal-IKEv1-ph2 pfs-group=modp2048
/ip pool
add name=pool1 ranges=172.20.2.2
/ip dhcp-server
add address-pool=pool1 interface=ether2 name=server1
/port
set 0 name=serial0
/ip address
add address=172.20.2.1/24 interface=ether2 network=172.20.2.0
/ip dhcp-client
add interface=ether1
/ip dhcp-server network
add address=172.20.2.0/24 dns-server=1.1.1.1 domain=workgroup gateway=172.20.2.1 netmask=24
/ip firewall filter
add action=accept chain=input connection-state=established,related
add action=drop chain=input connection-state=invalid
/ip firewall nat
add action=accept chain=srcnat dst-address=192.168.110.0/24 src-address=172.20.2.0/24
add action=accept chain=srcnat dst-address=192.168.111.0/24 src-address=172.20.2.0/24
add action=masquerade chain=srcnat out-interface=ether1 src-address=172.20.2.0/24
/ip ipsec identity
add peer=peer-->R1 secret=prova1@2
add peer=peer-->R3 secret=prova1@2
/ip ipsec policy
add comment=link-to-LAN-R1 dst-address=192.168.110.0/24 peer=peer-->R1 proposal=proposal-IKEv1-ph2 src-address=172.20.2.0/24 tunnel=yes
add comment=link-to-LAN-R3 dst-address=192.168.111.0/24 peer=peer-->R3 proposal=proposal-IKEv1-ph2 src-address=172.20.2.0/24 tunnel=yes
add comment=link-from_R3-to_R1 dst-address=192.168.110.0/24 peer=peer-->R1 proposal=proposal-IKEv1-ph2 src-address=192.168.111.0/24 tunnel=yes
add comment=link-from_R1-to_R3 dst-address=192.168.111.0/24 peer=peer-->R3 proposal=proposal-IKEv1-ph2 src-address=192.168.110.0/24 tunnel=yes
/system identity
set name=R2
/system note
set note="Questo Lab e' stato testato con Ip pubblico in dhcp client su ether1"
4. Configurazione PC2:
ip dhcp
set pcname PC2
save
5. Configurazione Router 3
Qui di seguito un export completo della configurazione del Router 3:
/interface ethernet
set [ find default-name=ether2 ] comment=LAN
/interface vlan
add interface=ether1 name=vlan80 vlan-id=80
/interface pppoe-client
add add-default-route=yes disabled=no interface=vlan80 name=pppoe-out1 \
password=HNNIWJCQ user=c1v
/ip ipsec profile
add dh-group=modp1024 enc-algorithm=aes-256 hash-algorithm=sha256 name=\
profile-IKEv1-ph1
/ip ipsec peer
add address=185.58.135.31/32 name=peer-->R2 profile=profile-IKEv1-ph1
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=proposal-IKEv1-ph2 \
pfs-group=modp2048
/ip pool
add name=pool1 ranges=192.168.0.2
/ip dhcp-server
add address-pool=pool1 interface=ether2 name=server1
/port
set 0 name=serial0
/ip address
add address=192.168.0.1/24 interface=ether2 network=192.168.0.0
add address=192.168.111.1/24 interface=lo network=192.168.111.0
/ip dhcp-client
add add-default-route=no interface=ether1
/ip dhcp-server network
add address=192.168.0.0/24 dns-server=1.1.1.1 domain=WORKGROUP gateway=\
192.168.0.1 netmask=24
/ip firewall address-list
add address=192.168.110.0/24 list=remote-lan
add address=172.20.2.0/24 list=remote-lan
/ip firewall filter
add action=accept chain=input connection-state=established,related
add action=drop chain=input connection-state=invalid
add action=accept chain=input dst-port=8291 protocol=tcp
add action=accept chain=input dst-port=22 in-interface=!pppoe-out1 protocol=\
tcp
add action=drop chain=input disabled=yes in-interface=pppoe-out1
/ip firewall nat
add action=netmap chain=dstnat comment=\
"NETMAP 19.168.0.0/24<-->192.168.111.0/24" dst-address=192.168.111.0/24 \
src-address-list=remote-lan to-addresses=192.168.0.0/24
add action=netmap chain=srcnat dst-address-list=remote-lan src-address=\
192.168.0.0/24 to-addresses=192.168.111.0/24
add action=accept chain=srcnat comment=allow_ipsec_to-R2 dst-address=\
172.20.2.0/24 src-address=192.168.111.0/24
add action=accept chain=srcnat comment=allow_ipsec_to-R1 dst-address=\
192.168.110.0/24 src-address=192.168.111.0/24
add action=masquerade chain=srcnat out-interface=pppoe-out1 src-address=\
192.168.0.0/24
/ip ipsec identity
add peer=peer-->R2 secret=prova1@2
/ip ipsec policy
add comment=link-to-LAN-R2 dst-address=172.20.2.0/24 peer=peer-->R2 proposal=\
proposal-IKEv1-ph2 src-address=192.168.111.0/24 tunnel=yes
add comment=link-to-LAN-R1 dst-address=192.168.110.0/24 peer=peer-->R2 \
proposal=proposal-IKEv1-ph2 src-address=192.168.111.0/24 tunnel=yes
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system identity
set name=R3
/system note
set note=\
"Questo Router e' stato utilizzato con PPPOE su vlan 80 e IP pubblico"
6. Configurazione PC3:
ip dhcp
set pcname PC1
save
Ti è piaciuta questa guida MIKROTIK IPSEC TRE SEDI OVERLAPPING?
Scrivi il tuo parere nei commenti o contattami attraverso la sezione Contatti.
Puoi supportare foisfabio.it con una piccola donazione oppure commenta e condividi questo contenuto.
Hai riscontrato errori in questa guida?? segnalacelo tramite la scheda CONTATTI
Guida redatta da Fabio Fois.
Copyright © 2024 foisfabio.it | Powered by Fabio Fois
Quanto è stato utile questo post?
Clicca su una stella per valutarla!
Voto medio 5 / 5. Conteggio dei voti: 1
Nessun voto finora! Sii il primo a valutare questo post.




Ha scritto “presenza di una sovrapposizione delle LAN dei Router 1 e 2” ma a giudicare dal diagramma di rete e dalla configurazioni le network in overlap sembrano essere quelle dietro a R1/R3.
Grazie comunque per l’ispirazione!
grazie per la segnalazione, ho corretto quanto. Saluti